ICAM Program Management 101
Introduction
The ICAM Program Management 101 explains how to plan and implement an Identity, Credential, and Access Management (ICAM) Program, as outlined in the Federal Identity, Credential, and Access Management (FICAM) Architecture. You’ll find content for ICAM program managers who need agency-level planning best practices to drive adoption of ICAM services within their organizations. You’ll also find information on how to govern the program, identify and communicate with stakeholders, manage risk, and other related topics.
The ICAM PM 101 will answer the most common ICAM program organization and management questions, including:
- How can I establish governance to ensure ICAM alignment at the agency level?
- Who are my key ICAM stakeholders?
- What best practices support ICAM implementation?
What Is ICAM Program Management?
“The interwoven technical architecture of the Federal Government creates complexity in managing access to resources, safeguarding networks, and protecting information…each agency must harmonize its enterprise-wide approach to governance, architecture, and acquisition.” - OMB Memorandum M-19-17
An agency’s ICAM program requires leadership to manage and oversee the program’s complex requirements, engage and collaborate with stakeholders, and apply proven risk management strategies to support the agency.
Primary Components
The following list includes the necessary components of an ICAM program.
- Program Governance and Leadership - Establish operational policies and requirements.
- Workstreams - Categorize tasks and assign them to the proper resources.
- Stakeholder Management - Identify and communicate with stakeholders.
- Communication Plan - Define and appropriately communicate program objectives and goals.
- Performance Management - Measure and report progress, effectiveness, and improvements.
- Privacy Requirements - Manage risks associated with handling personally identifiable information (PII).
Program Governance and Leadership
In any Identity, Credential, and Access Management (ICAM) program, you’ll need someone to develop, manage, and enforce agency-specific policies, processes, and performance measures.
About Governance
Governance is the set of practices that help your agency ensure that ICAM operations are successful. Governance helps your agency make decisions, manage enterprise policies, and improve efficiency.
An enterprise governance body develops and implements policies, rules, and procedures to manage the program. They collect data to monitor, analyze, and report on how well your ICAM program conforms with these policies, rules, and procedures. They also serve an important security role to quickly remediate any problems or vulnerabilities within the program before a security or privacy breach occurs. You’ll need to establish a recovery plan to ensure continuity of service to prepare for such an occurrence.
The pages that follow explain how to establish a formal identity management governance structure within your agency.
You don’t have to start from scratch. Instead, model your agency’s ICAM governance structure after existing programs. See the Governance Examples and Guidance section for agency steering committee and PMO examples as well as other authorities to consider.
Governance Body vs. Program Management Office
Governance bodies provide top-down leadership support and guidance across the programs within an agency, while Program Management Offices provide operational support for the day-to-day execution of the tasks within the program.
Program Governance Body
You can create an ICAM program governance body (for example, an Executive Steering Committee) to oversee your ICAM projects and workstreams and align ICAM services and management with your agency’s mission. The agency’s executive leadership will charter the governance body.
An ICAM program governance body can include the following personnel:
- Chief Information Officer (CIO)
- Chief Financial Officer (CFO)
- Chief Security Officer (CSO)
- Chief Data Officer (CDO)
- Human Resources (HR)
- General Counsel
- Chief Acquisition Officer (CAO)
- Senior Agency Official for Privacy (SAOP)
- Senior Agency Official for Physical Security (SAOPS)
- Agency component organizations that manage ICAM programs and capabilities
The governance body specifies the group’s authority to enforce changes, when necessary, to align ICAM technology, policy, and execution with your agency’s overall mission.
Roles and Responsibilities
We recommend you create a charter to govern the roles and responsibilities of your governance body. A governance body typically performs the following functions:
- Reviews and approves the program business architecture.
- Ensures proper resource allocation to ICAM programs and projects.
- Provides input for, or participates in, the critical development stages of the ICAM program.
- Provides strategic guidance for cost, schedule, performance, and technical solutions to ensure program success.
- Provides direction and counsel to the ICAM Program Management Office (PMO).
- Establishes cross-team collaboration to provide guidance, identify common agency challenges, establish best practices, and share solutions.
- Takes responsibility for overall stakeholder management, including stakeholders inside the agency, in other federal agencies, and outside the federal government.
- Creates and approves a process to review ICAM program changes and resolve disputes between ICAM and individual program offices.
- Reports on program status to oversight organizations, such as the Office of Management and Budget (OMB), Office of Inspector General (OIG), and Government Accountability Office (GAO).
- Reviews post-implementation evaluations to ensure that ICAM services and programs meet forecasted benefits and outcomes.
Component Governance
A component agency’s interdisciplinary team usually comprises the agency’s ICAM-related program managers and information technology (IT) experts. This team’s purpose is to provide ICAM-related recommendations to the governance body to help drive the ICAM program’s success via a bottom-up approach.
These groups leverage their experience and business context to provide the governance body with strategies, insights, and lessons learned around the following subjects:
- Risk management and mitigation.
- Impact of decisions on program executors.
- Improved buy-in across the agency.
Program Management Office
In addition to a program governance body, you can support the execution and operation of projects and workstreams with a Program Management Office (PMO).
An ICAM PMO complements the program governance body. Some agencies may not require both a program governance body and a PMO; however, larger agencies may need to separate governance and operational responsibility for effective ICAM operations. A PMO ensures individual components of the ICAM program operate efficiently and achieve the expected results within the defined budget and schedule.
For a PMO to be effective, it must:
- Be chartered to perform the functions as needed.
- Have the skills and expertise to implement the ICAM program.
- Have the support of executive leadership.
- Be allowed to use resources as required.
Organizationally, where should an ICAM PMO be located?
Since ICAM is technology and cybersecurity driven, an ICAM PMO should be structured under technology or cybersecurity leadership.
PMO Roles and Responsibilities
The PMO will typically be responsible for the following functions:
- Coordinating implementation efforts across ICAM stakeholders and component agency programs. For example:
- Identity management
- Credentialing
- Access management: physical access control systems (PACS)
- Access management: application access
- Personnel security
- Maintaining an enterprise ICAM perspective to ensure all component agency programs align with organizational objectives.
- Serving as a centralized point of contact for ICAM questions, issues, and concerns.
- Planning for and securing program funding to execute ICAM capabilities.
- Handling communications and outreach to both internal and external stakeholders.
- Managing and resolving program risks and issues across agency office, component, or bureau boundaries.
If your agency separates physical and logical security into separate offices, consider forming an ICAM guidance body with representation from each office to serve the function of a PMO.
PMO Governance Structure
PMOs generally follow standardized project management policies, processes, and methods. Within ICAM, a PMO facilitates communication, including sharing lessons learned inside and outside the agency. It may also serve as an advisor to other agency offices or programs impacted by the ICAM program on addressing ICAM as appropriate within other agency-wide capabilities. An ICAM PMO acts as a central point of contact for the agency’s ICAM program. The PMO is the primary authority to perform acquisition planning tasks and make procurement decisions.
The figure below represents a sample ICAM PMO structure. An agency should design this structure in a way that fosters communication, coordinates efforts, and aligns appropriately with the agency’s overall organizational structure.
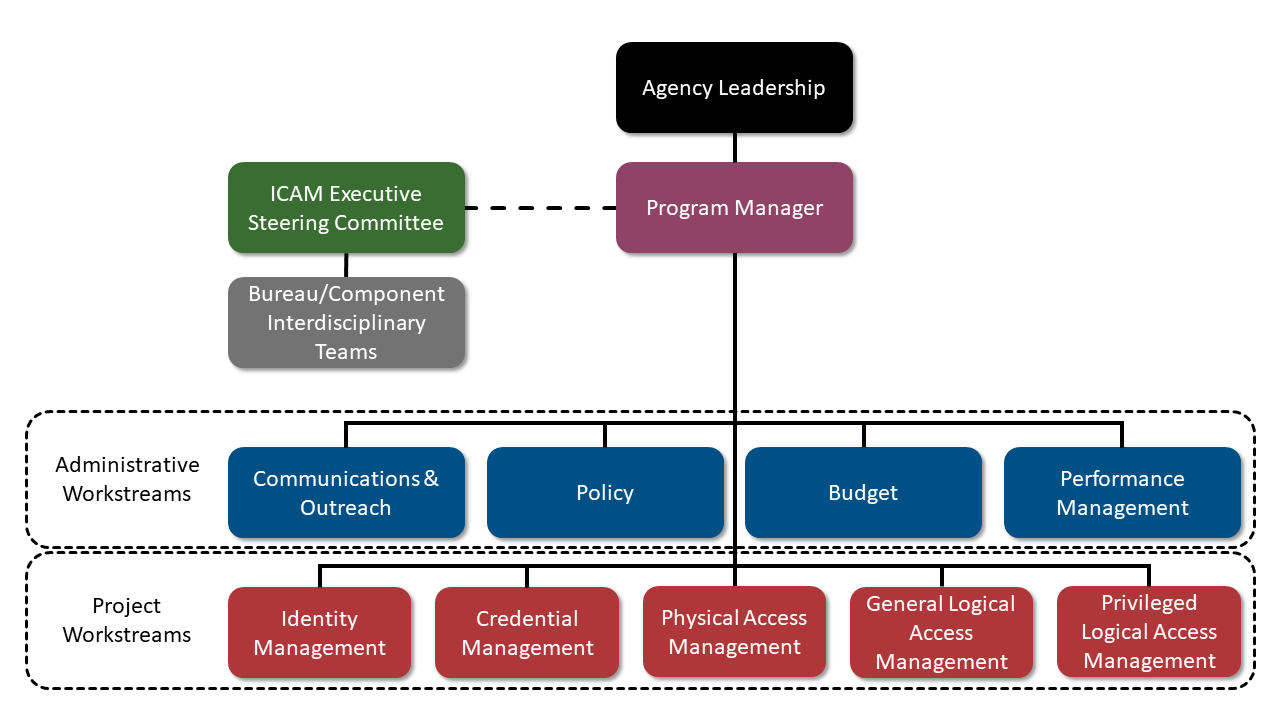
Workstreams
In the context of this guide, workstreams are the focus areas or projects within an Identity, Credential, and Access Management (ICAM) framework.
Many ICAM workstreams overlap with various divisions existing responsibilities. To promote the successful execution of your agency ICAM initiatives, divide and assign each workstream to employees already actively involved in a related area. Each workstream requires a task lead who manages the day-to-day activities of the workstream and provides the ICAM Program Management Office (PMO) with critical information about planning, development, deployment, and operations.
Thoughtful workstreams lead to the following outcomes:
- Enhanced efficiency.
- Streamlined overhead costs.
- Minimized redundancy of ICAM-related processes.
- Closer alignment with architecture and technical standards.
- Better communication and cooperation between interrelated programs.
- Consistent messaging to both internal and external stakeholders.
- Increased timeliness and accuracy of reporting.
- Greater agency-wide adoption.
- Reduced confusion and risk.
The following sections include descriptions of ICAM workstreams and responsibilities:
- Administrative Workstreams - Tasks related to governance and program management.
- Project Workstreams - Tasks related to day-to-day ICAM operations.
See the Agency Example section for a graphic depicting a sample ICAM program’s administrative workstreams.
Administrative Workstreams
Each administrative workstream is responsible for ICAM governance and both intra-agency and inter-agency communication.
| Outreach & Communications | Program Communications Plan development and execution, including: • Defining communication message types, media, target audience, and timing. • Communicating ICAM program concepts, activities, and progress to promote support for the implementation of improved ICAM capabilities. You should align with existing agency communication policies and leverage existing resources, if available, such as Business Relationship Managers. |
| Policy | Agency enterprise policy and standard operating procedure development and finalization. |
| Budget | Agency enterprise budget development, management, monitoring, and reporting. The Budget Workstream works closely with the agency’s Office of the Chief Financial Officer during the budget development and submission cycles. |
| Performance Management | Agency enterprise performance and metrics tracking, management, and reporting. |
Project Workstreams
Each project workstream is responsible for ICAM processes and systems related to various components.
| Identity Management | Digital identity data management. This includes modernizing the management of digital identities, such as HR modernization or enterprise identity management systems. |
| Credential Management | Credential lifecycle management activities. You may identify separate workstreams for various credential communities of interest, including agency Personal Identity Verification (PIV) and local facility access credentials, or public users. |
| Physical Access | Physical access control activities. This includes modernization efforts and security priorities in accordance with Interagency Security Committee (ISC) initiatives. |
| Logical Access | Logical access control activities. This includes authorization approaches for networks and major and minor applications, provisioning of accounts, determining identity assurance requirements, and determining authentication assurance requirements and related technologies or services in use. |
Agency Example
The following image depicts a series of ICAM administrative workstreams, adapted from the Department of Health and Human Services.
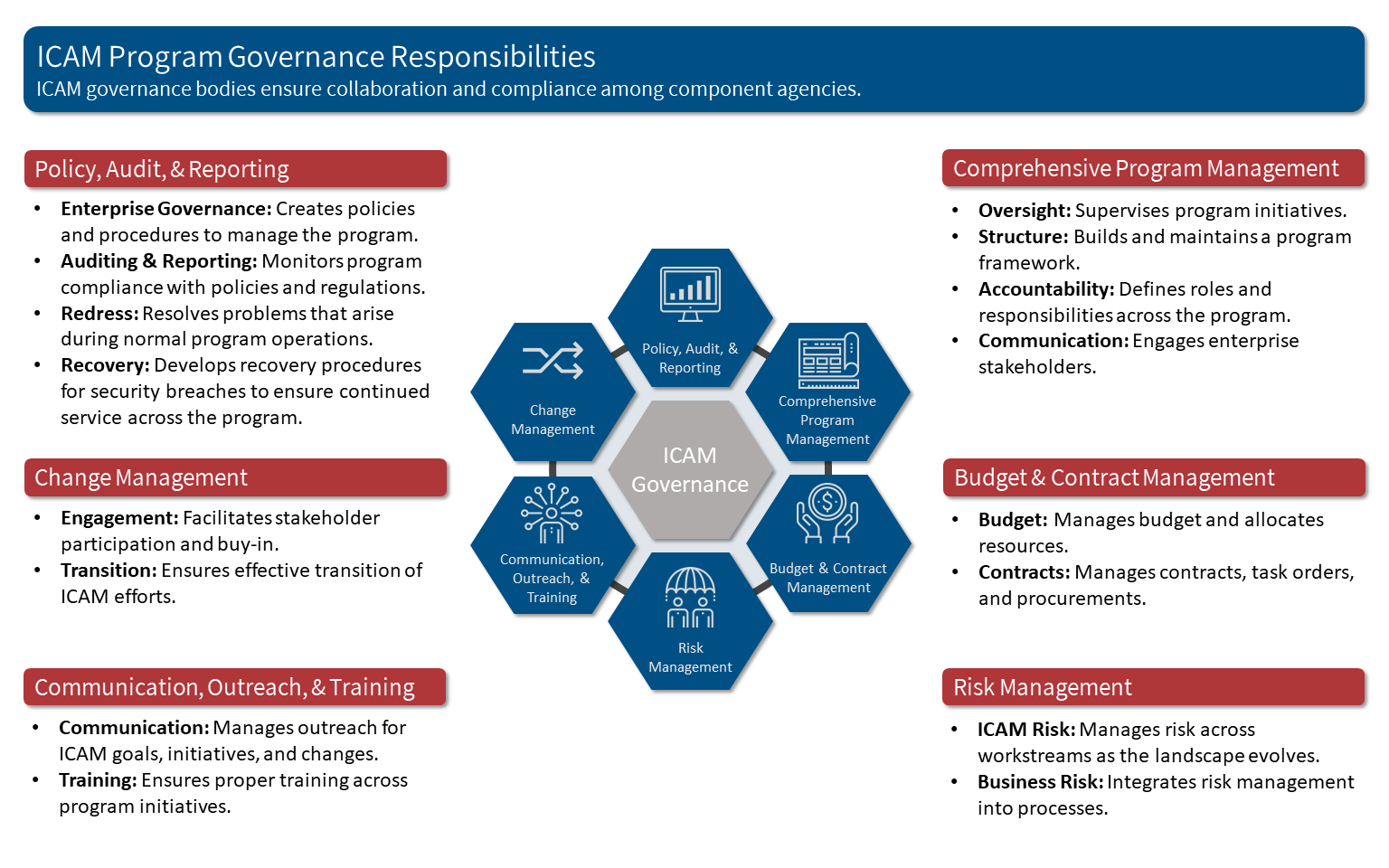
Stakeholder Management
A stakeholder is an individual or organization that has an interest in the program, either because the stakeholder is actively involved in the program or might be affected by the program’s outcome.
This page describes how to work with stakeholders by doing the following:
-
Identify Stakeholders - determine the individuals or agencies that will be involved or actively interested in your Identity, Credential, and Access Management (ICAM) program. The tables on this page provide a starting point to identify key ICAM stakeholders at the federal and agency levels.
-
Manage Stakeholders - establish effective communication and processes among your stakeholders.
Identify Stakeholders
Stakeholders can be internal or external to the agency. Internal stakeholders may include the program sponsor, steering committee, or governance board, and external stakeholders may include suppliers, investors, community groups, and other government organizations.
To understand the impacts of program decisions, you’ll need to identify all stakeholders for your mission delivery, not just those who may be positively affected by the project.
Federal Governance Bodies
| Office of Management and Budget (OMB) | Assists the President in overseeing the preparation of the federal budget and supervises its administration in Executive Branch agencies. Provides policy, direction, and oversight for the implementation of ICAM initiatives. Serves as the lead agency for E-Government implementation. |
| Federal Chief Information Officers (CIO) Council | Improves practices in the design, modernization, use, sharing, and performance of federal government agency information resources. Charters the work of the following: • Federal PKI Policy Authority. • Identity, Credential, and Access Management Subcommittee (ICAMSC). |
| Federal Chief Information Security Officer (CISO) Council | Oversees interagency CISO collaboration and communication. Identifies and recommends strategic high-priority IT security initiatives to advise the CIO Council and OMB. Focuses on the following strategic areas: • Identity management. • Comprehensive risk assessment and framework. • Vulnerability response. • Shared services. • Performance metrics. |
| Identity, Credential, and Access Management Subcommittee (ICAMSC) | Oversees identity management, secure access, authentication, authorization, credentials, privileges, and access lifecycle management. Is a subcommittee of the CISO Council. Provides opportunities for agencies to raise issues and challenges associated with the planning, implementation, and operations of ICAM programs and solutions. Recommends new ICAM policies and updates existing ones. Develops specific tools to assist agencies’ abilities to meet ICAM policy objectives and overcome identified ICAM implementation challenges Fosters cross-government collaboration on information sharing, lessons learned, and best practices related to ICAM. |
| Federal Privacy Council | Improves agency practices for the protection of privacy. Serves as an interagency coordination group for Senior Agency Officials for Privacy and Chief Privacy Officers in the federal government, promoting adherence to the letter and spirit of laws and best practices advancing privacy. |
| Department of Homeland Security (DHS) | Oversees government-wide and agency-specific cybersecurity implementation and reporting for information systems that fall under the Federal Information Security Management Act (FISMA). Provides adequate, risk-based, and cost-effective cybersecurity. |
| Office of Personnel Management (OPM) | Develops policies and procedures to ensure the effective, efficient, and timely completion of investigations and adjudications when determining if candidates for employment or direct contract support for federal agencies are eligible for access to federal resources. Serves as the suitability executive agent for the federal government. |
| Suitability and Security Clearance Performance Accountability Council (PAC) | Develops policies and procedures related to suitability, fitness, and clearance determination activities and processes. Serves as the most senior policy-making entity for the security and suitability reform effort and provides final determinations for resulting reports. |
| Interagency Security Committee (ISC) | Develops standards, policies, and best practices to enhance the quality and effectiveness of physical security in, and the protection of, nonmilitary federal facilities in the United States. |
| National Science and Technology Council (NSTC) | Coordinates science and technology policy across the federal research and development enterprise. |
Internal Standards Body
| National Institute of Standards and Technology (NIST) | Promotes U.S. innovation and industrial competitiveness by advancing measurement science, standards, and technology. |
External Service Customers
| American Public and Businesses | Individuals and businesses that require access to government systems and resources. The governmentwide approach to ICAM must address the varying needs of these communities, focusing mainly on the characteristics of the two user segments: Government-to-Citizen (G2C) and Government-to-Business (G2B). |
| State, Local, Foreign, and Tribal Governments | Governments that transact business on behalf of their constituencies or higher levels of government. Partner with the federal government on identity management initiatives. |
Agency-Level Stakeholders
| Agency Partners and Affiliates | Contractors working on behalf of the federal government and affiliates that do business with or consume the services provided by federal agencies. Portions of this population use PIV credentials to access agency facilities and information systems while others use non-PIV credentials and require only occasional access to agency assets. |
| Business Process/System Owners | Individuals within an agency responsible for managing a set of activities, programs, and systems that are critical to operations and use ICAM services. |
| General Counsel | Provides legal oversight over an agency’s ICAM program, administering security clearance review programs and ensuring that ICAM programs abide by all applicable laws and regulations. |
| Human Resources (HR) | Collects information on federal employees. Creates a digital identity for each employee within the agency’s HR applications. |
| Office of the Chief Financial Officer (OCFO) | Processes and submits budget requests for ICAM investments. Ensures that each agency investment leverages ICAM requirements and tools. |
| Office of the Chief Information Officer (OCIO) | Coordinates with the agency’s Chief Financial Officer (CFO) to ensure that the IT programs and activities are cost-effective. Ensures that appropriate security controls are applied, determines how the ICAM solution will impact the security of existing applications, and incorporates ICAM into the agency’s Enterprise Architecture (EA). |
| Office of the Chief Information Security Officer (OCISO) | Develops, employs, and publishes security policies, programs, and standards to guard the agency’s personnel, property, facilities, and information. Has leadership and authority over security policy and programs within the agency and can coordinate with the Personnel Security and Physical Security divisions. |
| Personnel Security | Coordinates with managers’ HR departments to determine position sensitivity levels for each position occupied within the agency. Coordinates with OPM to ensure all agency employees and contractors receive an appropriate background investigation and periodic reinvestigation. |
| Physical Security | Manages the security of agency buildings, such as resolving conflicts concerning entry to facilities and verifying that those seeking to gain access to federal buildings are authorized to do so. |
| Privacy Office | Administers policy to govern the use, collection, storage, and dissemination of personally identifiable information (PII) for all agency employees, contractors, and affiliates. Maintains an agency’s System of Records Notices (SORNs) and supports Privacy Impact Assessments (PIAs) for all IT investments, including ICAM. |
| Unions | Frequently involved in matters related to ICAM processes that collect personal information or introduce additional requirements for background investigations. |
Manage Stakeholders
Stakeholder management involves coordination, collaboration, and communication within the agency. Each stakeholder group has a distinct mission requirement and performs duties in support of the overall agency mission. These stakeholders have different viewpoints that may conflict with each other or the overarching ICAM program objectives, and decisions made in one program area may impact another.
To encourage collaboration, develop working groups that comprise stakeholders across the program. Stakeholders in these working groups incorporate their needs into the ICAM program and share implementation lessons learned in other ICAM implementations to reduce overall program risk and increase efficiency in implementation.
You can also stand up smaller focus groups or tiger teams devoted to specific program issues or direct implementation support. You’ll promote consistency and stakeholder buy-in by encouraging better understanding, inclusion, and ownership in the program.
Communication Plan
A communication plan outlines an Identity, Credential, and Access Management (ICAM) program’s objectives, goals, themes, and approach. You should create a communication plan early in the lifecycle to communicate consistently and effectively with users and stakeholders.
The following table includes a summary of some common communication activities you should prioritize in your program.
| Educational resources for stakeholders and users | Various stakeholder groups | Website, collaboration portal |
| Ad hoc updates for system rollout events and changes | User population | Email, newsletter bulletin |
| Leadership briefing highlighting objectives and status | Agency leadership | Slide presentation, meeting |
| Messages from leadership | ICAM implementers | Memo, email |
| Awareness materials explaining workstream features and milestones | User population | Social media, videos, brochures, posters |
| Lessons-learned workshops | ICAM implementers | Meeting, teleconference, webinar |
| Large-scale gathering (agency ICAM conference or all-hands) | ICAM implementers, User population | Meeting, teleconference, webinar |
You should tailor the messages and delivery methods to the stakeholders. The goals of this plan include informing and involving stakeholders by providing regular and well-structured communications, fostering and maintaining stakeholder support, and reducing risk.
Lesson Learned
Communicate changes that impact users early and often and across multiple messaging vehicles.
Performance Management
Program leadership and stakeholders need tools to monitor progress, determine program effectiveness, and identify areas of improvement. To accomplish this, assign performance measurements to your agency’s Identity, Credential, and Access Management (ICAM) program.
OMB Memorandum M-19-17 identifies two key performance measurements that help agencies establish effective ICAM governance:
1) Outline enterprise-level performance expectations for cybersecurity and risk management through each user’s lifecycle, including changes in the user’ s access privileges. 2) Streamline and automate enterprise-level performance reporting, aligned with existing and planned reporting and analytics structures and tools, such as the Continuous Diagnostics and Mitigation (CDM) dashboards and Federal Information Security Management Act (FISMA) reporting.
We also recommend that you follow government-wide ICAM metrics, such as Cross-Agency Priority (CAP) Goals and CIO FISMA metrics. These metrics are an existing foundation for reporting requirements and performance measurement and accomplish the following goals:
- Reduce the time needed to prepare external reports.
- Provide synchronized data points for government-wide leadership, agency leadership, and program managers.
- Represent comprehensive measurements that cover transactions between the federal government and its employees, contractors, business partners, and citizens.
Implementation Tips
Incorporate relevant metrics in your Exhibit 300 for any ICAM investment to track investment results and communicate value to your agency.
Tie your agency’s ICAM program accomplishments directly to the responsible individual’s yearly performance plan. This helps leadership and management assume ownership and feel accountable for the ICAM program’s success.
Privacy Requirements
All federal agencies and programs that collect, retain, or use personally identifiable information (PII) are required to complete and maintain program documents to support these activities.
“Federal information is a strategic asset subject to risks that must be managed to minimize harm; Protecting an individual’s privacy is of utmost importance. The Federal Government shall consider and protect an individual’s privacy throughout the information life cycle; While security and privacy are independent and separate disciplines, they are closely related, and it is essential for agencies to take a coordinated approach to identifying and managing security and privacy risks and complying with applicable requirements.” - OMB Circular A-130
OMB Circular A-130 – Appendices I and II, establish requirements and guide agencies on how to coordinate information security and privacy programs to interact cohesively and describe responsibilities for protecting federal information resources and managing PII, giving agency heads the ultimate responsibility of meeting the requirements in this circular. Agency Identity, Credential, and Access Management (ICAM) leaders should coordinate with their Senior Agency Official for Privacy (SAOP) and privacy office to review and implement privacy principles, procedures, and guidelines. To learn more about the processes you should complete so your agency can meet key privacy requirements, please view OMB Circular A-130.
Apply Fair Information Practice Principles
ICAM programs collect, store, share, and maintain PII. As such, your agency must actively support privacy protections and the widely-recognized Fair Information Practice Principles (FIPPs). Under the Privacy Act of 1974, based on FIPPs, your agency must have processes and procedures governing the use of PII. When you implement your ICAM program, determine whether you must adjust processes and procedures due to a new use of PII.
Privacy Tip
We encourage you to provide redress mechanisms even when the Privacy Act doesn’t require them. Promote confidence in your users’ interactions with the government by allowing them to provide feedback and rectify issues with their PII.
The table below describes each of the FIPPs and gives practical implementation considerations for applying them within an ICAM program.
FIPPS Implementation Considerations
| Access and Amendment | Provide individuals with appropriate access to PII and opportunity to correct or update PII. | Make it simple to access individual PII. Provide Privacy Act-compliant procedures to: • Report and correct information that is inaccurate, lost, or compromised. • Mitigate damages resulting from incorrect authentication or unauthorized access. Redress mechanisms enhance confidence in the program and promote individual participation. |
| Accountability | Comply with these principles and properly train employees and contractors who use PII. Monitor, audit, and document the actual use of PII to demonstrate compliance with these principles and all applicable privacy protection requirements. |
Establish accountability measures to appropriately apply FIPPs to protect users’ privacy effectively. These can include ICAM program audits and reviews by agency privacy and security officials. Address accountability for specific requirements, such as the M-07-16 requirement for annual certification of training for employees who handle PII. Clear accountability promotes confidence in ICAM programs. |
| Authority | Create, collect, use, process, store, maintain, disseminate, or disclose only the PII that your agency has the authority to do so. Identify this authority in the appropriate notice. | Identify a specific authority to create, collect, use, process, store, maintain, disseminate, or disclose PII. |
| Minimization | Collect only PII that is directly relevant and necessary to accomplish the specified purpose(s) and retain PII only for as long as is necessary to fulfill the specified purpose(s). | Collect only the information required to carry out ICAM business functions. Wherever possible, use assertions of an individual’s identity in lieu of identifying data elements. For example, if an application has an age limit, the program should ask for proof of age rather than the exact birth date. Determine how long your agency will retain specific categories of information and implement procedures to destroy the information at the end of the retention period. |
| Data Quality and Integrity | Ensure that PII is accurate, relevant, timely, and complete. | Identify and implement means to ensure that PII is accurate, relevant, timely, and complete, including allowing individuals to correct inaccuracies in their information. |
| Individual Participation | Involve the individual in the process of using PII. When possible, seek individual consent to collect, use, disseminate, and maintain PII. Your agency should also provide mechanisms for appropriate access, correction, and redress regarding use of PII. | If your agency interacts with the public face to face or engages by paper or telephone, some people will not feel comfortable adopting technological processes. Your agency should continue to offer physical alternatives for procedures that are not inherently technology-based. Provide Privacy Act-compliant procedures to: • Report and correct information that is inaccurate, lost, or compromised. • Mitigate damages resulting from incorrect authentication or unauthorized access. Redress mechanisms enhance confidence in the program and promote individual participation. |
| Purpose Specification and Use Limitation | Use PII solely for the purpose(s) specified in the notice. Sharing PII should be for a purpose compatible with the purpose for which the PII was collected. | The Privacy Act generally requires that once a person consents to the collection of his information for a specific, stated purpose, that information can only be used for that purpose. This is important to remember when sharing information between programs. If the programs have different purposes, you likely shouldn’t share information without additional consent from the user. Consider this limitation when you create your agency’s privacy ICAM program notices. |
| Security | Protect PII through safeguards against risks such as loss, unauthorized access or use, destruction, modification, or unintended or inappropriate disclosure. | Your agency must ensure the security of information at all stages (collection, transmission, storage, destruction) in accordance with various legal and policy requirements, such as FISMA and OMB M-07-16. Examples of techniques for securing data include: • Encryption. • Strong authentication procedures. • Time-out functionality. • Minimum security controls to make information unusable by unauthorized individuals. |
| Transparency | Be transparent about the information your agency collects and shares, and notify the individual regarding collection, use, dissemination, and maintenance of PII. | A foundational principle in federal privacy law is that people have the right to know what information the government collects and retains about them and, to a great extent, the right to control how that information is used. Consider this principle and ensure the following before each occurrence of information collection or transmission: • Inform the user about which information elements you’ll collect. • Inform the user who will receive the information. • Inform the user about how you’ll use the information. • Allow the user to affirmatively choose to participate before you transmit any information. |
PM Implementation Examples
We recommend leveraging existing resources to establish your Identity, Credential, and Access Management (ICAM) program and define roles and responsibilities across the enterprise.
On this page, you’ll find guidance to help you implement your ICAM program:
Agency Examples
Governance Structure
The figure below provides an example of an ICAM governance and program management structure implemented by the Department of Health and Human Services (HHS).
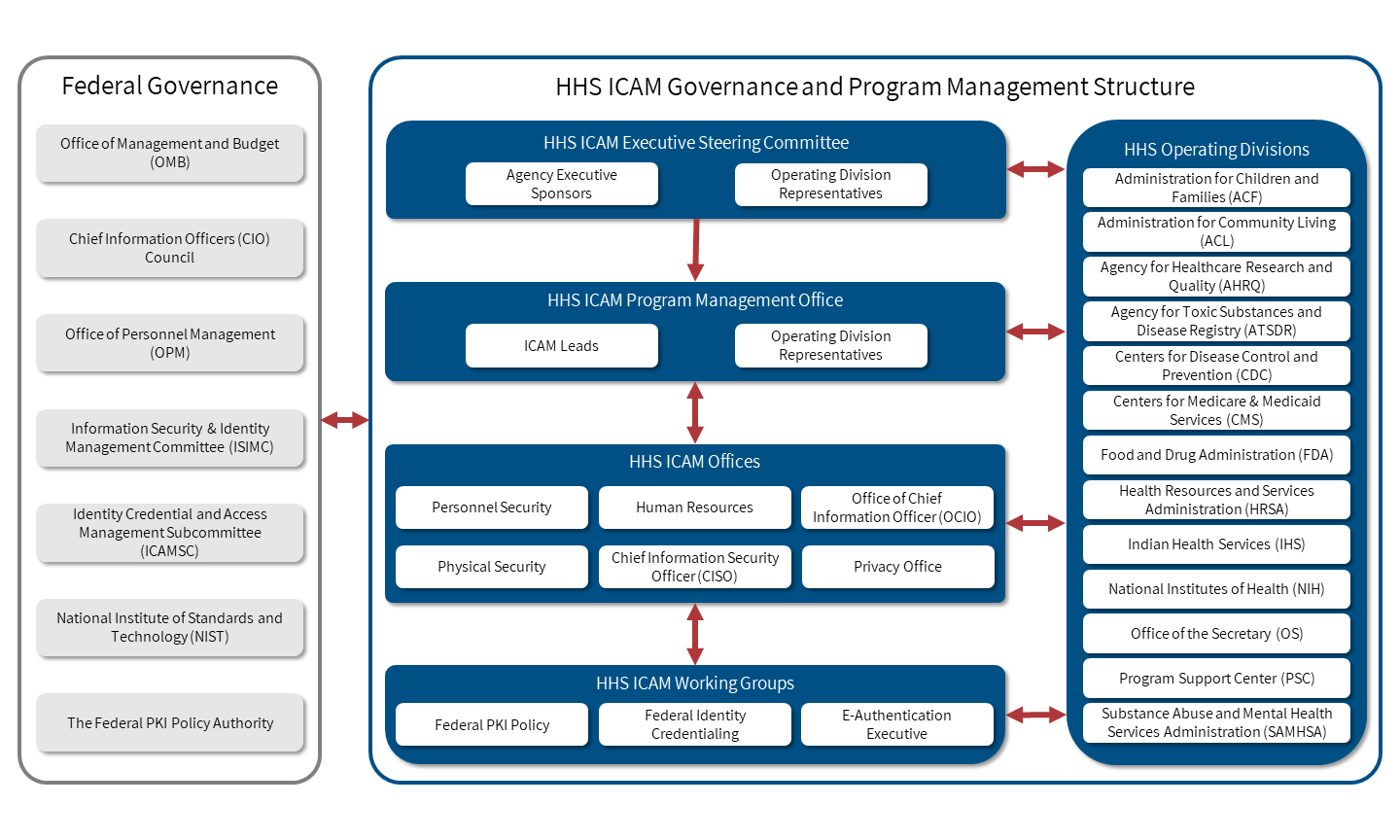
ICAM PMO Charter
For an example of an ICAM Program Management Office (PMO) charter, download the HHS ICAM PMO Governance Charter (MS Word, May 2019)
Authorities to Consider
Executive Order (EO) 13800 – Strengthening the Cybersecurity of Federal Networks and Critical Infrastructure
EO 13800 provides requirements to strengthen the cybersecurity of federal networks, including holding agency heads accountable for managing cybersecurity risk to their enterprises.
“Effective risk management requires agency heads to lead integrated teams of senior executives with expertise in IT, security, budgeting, acquisition, law, privacy, and human resources.” - EO 13800 - Section 1,b,v.
NIST Risk Management Framework
The NIST Risk Management Framework (RMF) provides an approach to managing organizational risk.
Federal Information Technology Acquisition Reform Act (FITARA) and OMB M-15-14
FITARA, a U.S. law passed in December 2014, gives federal agency CIOs significant roles in IT investments including:
- Annual and multi-year planning
- Budgeting
- Reporting
- Management
- Governance
- Oversight functions
OMB M-15-14 provides implementation guidance for FITARA and assists agencies in establishing effective governance.


